Destination Resilience

The Appleton Greene Corporate Training Program (CTP) for Destination Resilience is provided by Mr. Wetter Certified Learning Provider (CLP). Program Specifications: Monthly cost USD$2,500.00; Monthly Workshops 6 hours; Monthly Support 4 hours; Program Duration 12 months; Program orders subject to ongoing availability.

Personal Profile
Mr. Wetter holds a Master’s Degree in Business Management from Münster University, Germany. Before he founded his Management Holding, he looked back on a successful career in Europe. During the last 20 years he gained major experiences in several industries. As leading manager, he worked in the Consumer and Media Industry for Top-Management. Since the last years, he specializes in Cyber Security Management and serves as a Lieutenant Colonel in the German Armed Forces Reserve, Cyber Command. As a pilot he loves to travel fast, he embraces lifelong teaching and learning, guided by the motto:
“semper gradum praemisit – always one step ahead”
To request further information about Mr. Wetter through Appleton Greene, please Click Here.
(CLP) Programs
Appleton Greene corporate training programs are all process-driven. They are used as vehicles to implement tangible business processes within clients’ organizations, together with training, support and facilitation during the use of these processes. Corporate training programs are therefore implemented over a sustainable period of time, that is to say, between 1 year (incorporating 12 monthly workshops), and 4 years (incorporating 48 monthly workshops). Your program information guide will specify how long each program takes to complete. Each monthly workshop takes 6 hours to implement and can be undertaken either on the client’s premises, an Appleton Greene serviced office, or online via the internet. This enables clients to implement each part of their business process, before moving onto the next stage of the program and enables employees to plan their study time around their current work commitments. The result is far greater program benefit, over a more sustainable period of time and a significantly improved return on investment.
Appleton Greene uses standard and bespoke corporate training programs as vessels to transfer business process improvement knowledge into the heart of our clients’ organizations. Each individual program focuses upon the implementation of a specific business process, which enables clients to easily quantify their return on investment. There are hundreds of established Appleton Greene corporate training products now available to clients within customer services, e-business, finance, globalization, human resources, information technology, legal, management, marketing and production. It does not matter whether a client’s employees are located within one office, or an unlimited number of international offices, we can still bring them together to learn and implement specific business processes collectively. Our approach to global localization enables us to provide clients with a truly international service with that all important personal touch. Appleton Greene corporate training programs can be provided virtually or locally and they are all unique in that they individually focus upon a specific business function. All (CLP) programs are implemented over a sustainable period of time, usually between 1-4 years, incorporating 12-48 monthly workshops and professional support is consistently provided during this time by qualified learning providers and where appropriate, by Accredited Consultants.
Executive summary
Destination Resilience
History
Since years we can experience that companies focus on growth and developing new products for markets they researched. The percentage of companies which failed or did not develop parallel to the average market had a lack of resilience towards external impacts or superior internal problems. Those companies which invested in consultancy concentrating on prevention and resilience, to make it short, developed much better and did not suffer so much from these interferences. With the digitalization the fragility of companies raised due to cyber threats and data problems. Resilience is the key purpose the federal defense concentrates on during peace.
Exercises, planning and execution as well as a pre-defined consistent process of communications which enables the huge defense organization to respond quickly when an attack happens. The consultancy and outline process helps companies to set up their resilience program and develop their individual cyber crisis management playbook. Even if it is individual the basics and the guidelines for an efficient cyber resilience management are general and can be taught within a structured process during a certain time invest and the group of managers responsible for the efficient execution of the crisis management. It is very important that this will be approached within a holistic approach from top to middle management and base.
Most companies do have an incident response team and already implemented software to optimize the process. But it can also be recognized that staff fluctuation and the lack of a permanent reconfiguration is missing. That is the reason why it is recommended investing more into the general structure and stable implementation. With this program the selection of success factors from resilience programs can be yours. When a high severity cyber incident strikes an organization, the financial, operational, and reputation impacts can be significant, if not catastrophic. Organizations can reduce these risks and expediate the return to normal operations using a cyber crisis management plan (CCMP).
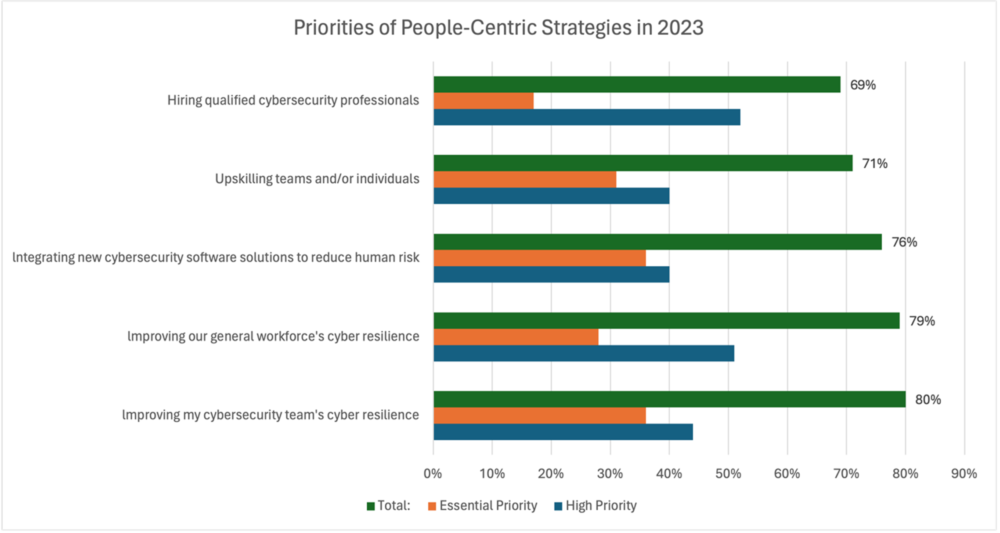
“Managers see upskilling existing teams and/or individuals as a higher priority than hiring new cybersecurity professionals. This strategic emphasis highlights the skills gap in the market, the benefit of staff knowing the organization’s culture, and the value of driving resilience with better team-level skills and experiences rather than merely adding new people with untested resilience capabilities.” Osterman Research (2023)
Figure 1 Priority of People-Centric Strategies in 2023
Percentage of respondents indicating “high priority” or “essential priority”
Source: Osterman Research (2023)
Current Position
Currently we can experience that due to crisis all around the world the number of damages doubled within the last three years. It is not a matter of “will you be attacked” by a hacker or hacking organization but “how hard” will you be attacked when f. ex. a ransomware attack successfully strikes your datacenter and is ready to leak important internal company material. This causes not only productivity and turn over because you’re not able to work as usual, but it also costs reputation and your unique position might vanish forever when relevant data gets into the hand of a competitor.
Last but not least you will have to pay money to the federal data protection department and it is clear that all the management will suffer from incredibility and that top management has one leg in jail. You might frequently recognize that in your industry sector companies suffer from, but you cannot estimate how dangerous is your actual situation and you also do not know where to start? But the part which ignores this and has not a stable cyber crisis infrastructure gets hit hard.
Cyber-attacks are like hurricanes. They appear when you do not expect them and when they pass your doors almost nothing will be like the day before. That is why we developed this program and give the opportunity to all companies to reflect their actual lines of communication, internal audits, process and software tools for prevention and cyber crisis management. It will also guide you to a better way of communication during cyber crisis which can also be used for other types of crisis as well. The stakeholder view will be widened and the relevance of external partners and institutions – we embedded at the same time.
Traditional information technology incident response plans often fail to consider the cross-organizational activities that need to be performed to remain resilient. Developing a cyber crisis management plan requires organizations to take a holistic approach to cyber crisis planning. By proactively acting to build a cyber crisis management plan, a broader, carefully considered, integrated and validated plan can be developed to meet an organization’ s unique demands before the crisis strikes.
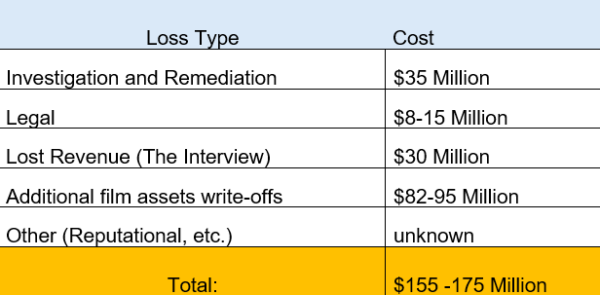
In 2014, Sony Pictures suffered a devastating and highly publicized cyberattack related to its planned release of the controversial film “The Interview”, which intelligence reports later attributed to a nation-state attacker. As employees were locked out of thousands of company computers and hundreds of servers, their systems’ memory was wiped clean while sensitive personal information and valuable corporate assets were stolen and eventually released online. In time, questions concerning the adequacy of Sony’s cybersecurity program became a prominent topic for cybersecurity experts as well as business leaders, as its IT decisions left the company and its stakeholders vulnerable.
Figure 2 – Sony Picture Case – Estimated loss due to cyber attack
Source: School of International and Public Affairs – Case Consortium,
Columbia University, SIPA-21-0023.1
Future Outlook
Even if the actual program will be a longtime investment it needs to be implemented carefully into your company. The consultancy which paths the process you can also secure that during the next years the stability of your company can grow. With refresher, auditing and communication training as well as cyber crisis reality training as well. We already have this in mind and this should be clear when you look on the outline plan of the program. At the end you will have a general process, resources and responsibilities and the ability to develop your resilience infrastructure on your own.
Continuity-Management and the necessities to make it happen will be more and more important so that we lay the base for stability and potential future development by the execution of this program. We also want to adapt all general features to your companies characteristics and you will have the possibility to navigate through the program with the velocity and focus you need. The workshop modules are logical and step by step but also agile enough to set individual focus areas. It is estimated that within the next years the annual damage due to cyberattacks will extremely accelerate. The investments in protection need to develop equally and each little investment will reduce much more damage.
Imagine just one day earlier your production can restart or your email server is ready to distribute customer bills, you will be glad. Velocity and acceleration as well as the ability to reduce stress and communication inefficiencies or misunderstandings is key in the game. The development of a training program for your organization and the implantation process as well as the regular execution will guide you in the future and by help of this program.
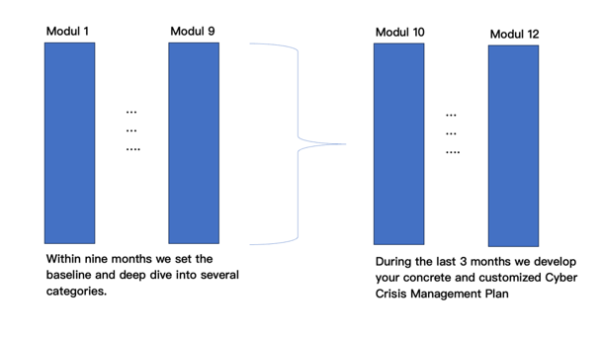
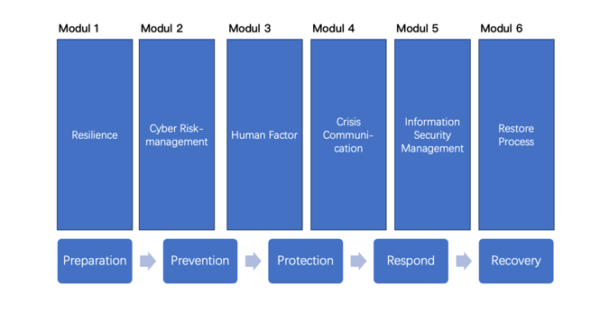
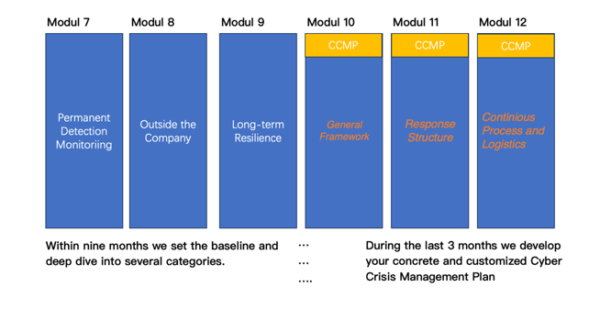
These twelve workshop modules exactly focus on your own redesigned Cyber Crisis Management Plan (CCMP) you will develop within the last three workshops. The nine plus three patterns will help your company to first deepen relevant aspects of organizations resilience. Going from a wide angle to a deep dive within each module your workshop attendances will get to “know, play and work” with the success factors of cyber resilience.
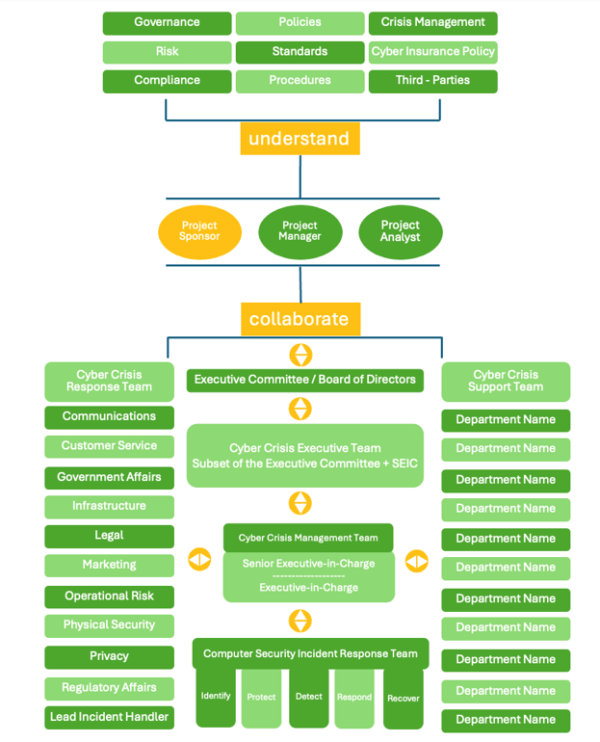
Figure 3 shows a holistic approach of a Cyber Crisis Management Plan. The adaption and concretization to your company will be one of the major goals during our process. Setting up the roles, structure and responsibilities at latest stage of your company and being fit for the future implementation is a key benefit of the program.
Figure 3 – Example of an efficient organizational implementation
– Holistic approach of Cyber Crisis Management – Project Team Members Overview
Source: Cyber Crisis Management Planning – own graphic based on Jeffrey Don Crump
Curriculum
Destination Resilience – Part 1- Year 1
- Part 1 Month 1 Roadmap to Resilience
- Part 1 Month 2 Cyber Risk Management
- Part 1 Month 3 Role of the Human Factor
- Part 1 Month 4 Crisis Communication
- Part 1 Month 5 Information Security Management (ISM)
- Part 1 Month 6 The Restore Process
- Part 1 Month 7 Permanent Detection Monitoring
- Part 1 Month 8 Outside the company
- Part 1 Month 9 Ongoing resilience
- Part 1 Month 10 Purpose and general framework (CCMP)
- Part 1 Month 11 Response Structure (CCMP)
- Part 1 Month 12 Response Continuous Process and Logistics (CCMP)
Program Objectives
The following list represents the Key Program Objectives (KPO) for the Appleton Greene Destination Resilience corporate training program.
Destination Resilience – Part 1- Year 1
- Part 1 Month 1 Roadmap to Resilience – The roadmap to resilience starts with the definition of resilience itself. Key performance indicators and measurements will be discussed and set into the context of your company. Understanding the general resilience cycle is key for any further discussion and will help your team in any case, whether it is business or just for living. During the second part of the first module, we will focus on cyber resilience and break it down. Therefore, we need to discuss different types of cyber threats and areas of protection like trust, integrity and authentication. With the Sony Picture Case we will analyze how a cyberattack effects companies and which critical stages a company must go through. With the practice “analyze areas of mitigations” all candidates will be sensibilized and motivated for the follow up workshops. Each module will end with a short evaluation to adjust the following workshop. We want the roadmap to resilience your individual roadmap and can adapt focus areas from workshop to workshop.
- Part 1 Month 2 Cyber Risk Management – We will discuss cyber risk assessments, the identification of theses as well as your asset management and resources. What are your “crown jewels” and where to focus on in the future. What budget goes where? The IRBC Gap Analyses will help to get a better understanding and the Single-Point-of-Failure concept will be deep dived. The practice of this workshop then evaluates your own company in terms of cyber risk management. In the second part of this workshop we will discuss existing cyber risk management and governance principles such as ISO and NIS standards. Ending with a conclusion we can practice which standards will be useful for your company in the future and make a priority list of it. This will give a good picture of the status quo and the potential step by step resilience destiny.
- Part 1 Month 3 Role of the Human Factor – Cyber Crisis Management is done by people. Stress is a key parameter all your employees must handle. We will deep dive into the “Stress” and “Awareness” topic and will discuss areas of corruption and sabotage. For prevention we will focus on physical and soft tools and develop parameters for your influence matrix. Understanding and handling the “Issue Stake- Holder Management” will be part of the second part of this workshop. How to build cyber risk teams, roles and documents. Where is the difference between an incident and a crisis, what legal aspects do we have to consider? The set-up of crisis staff will be the practical part and we round it up with the “Highlander Principle” and the “FOR-DEC Scheme” to give success a name and the chance to be remembered when necessary.
- Part 1 Month 4 Crisis Communication – We will discuss the success factors of cyber crisis communication within the stakeholder evaluation approach. Which means we will extract your major stakeholders and bring it into the context with the companies most important assets. The practice part will lead to a matrix you will always need and which needs to be developed over time. If you do not have it yet. Now it is time to bring it on the desk. Second, we will make a business impact analyses in context of potential threats like DDOS or Ransomware attacks. What impact has each of these incidents on your crown jewels? How will you communicate and who will communicate with whom and by use of what type of communication – have you already thought of it when your traditional ways of communication are out of order. You need a plan B and this needs to be developed when a crisis hasn´t happened yet. In this workshop now and not when the storm is already there. In the practical part we will break down to critical sentences and its impact of your stakeholders when you do not use the right way of communication. What buzz words should you avoid and how should your management communicate better.
- Part 1 Month 5 Information Security Management (ISM) – After a general introduction into ISM we will talk about prevention and actions your company might already take and potentially want to strengthen. We will talk about not only about cryptography, access management and the Zero Trust Concept. In the second part Cyber Incident Response will be analyzed and the result of our practice shall be a gap analyses of your existing ISM and the one you probably wish to implement soon because you now detect the focus areas and know where an investment has an effective impact. What kind of Crisis Management tools are available and what are the advantages and disadvantages of each of these. Is the question web-based tool versus physical tools or do we have to adjust these tools in context of your organizational structure? How will your documentation look like and when and how will it be distributed. The task is to decide and evaluate the use. Finally, this workshop discusses the role of a situation center as well as the realization of a crisis room. Can the SOAR concept be your destination? This would mean a secure, orchestration, automation and response throughout your whole company.
- Part 1 Month 6 The Restore Process – We will discuss what data safety concepts exist an evaluate in context of your actual companies’ concept. The Recovery Point (RTO) Objective in comparison with the Maximum Tolerable Period of Disruption (MTPD) will be discussed. How will you successfully get back to continuity management is at least as critical as managing the incident itself. The requirements of availability and the potential dimensions – time, quality and amount will be adjusted in the practical part. What are the success factors of your recovery plan and how does it look like, now and in the future? What adjustments will you focus on? This output shall help to reduce risk and raise resilience.
- Part 1 Month 7 Permanent Detection Monitoring – This is not only a task, but also a necessary process which needs to be implemented in your company. We will discuss the measurements and adjustments, the involved teams and tools as well as the recipients. Do you have to take actions or is your company already ready? Within the practical part we have time to figure out the baseline of measurements and define metrics and actions as well as the suitable lines of communications. You decide whether the output can be a complex mind map or a simple spread sheet.
- Part 1 Month 8 Outside the company – The stakeholder approach already told us to list all potential interfaces. Where do we get information about potential threats, in which communities do we need to cooperate, where are our “friends” and how close do we want to let them in? This leads to the question what services can we outsource to minimize risk and to what costs? We will talk about the insurances and their policies as well as the use of audits, testing and whistle blower concepts. A matrix which evaluates the relevance of the services at the end of workshop 8 will be your output.
- Part 1 Month 9 Ongoing resilience – How often should you train, which scenarios are useful and how do you train effectively in terms of cyber resilience. Deploy your new training plan and consider the content and training strategy. Are games, tabletop exercises and special days useful at your company. Which tools will you use in the future and how will you implement these? A one-year training catalogue, content and recipients as well as responsibilities will be the output of workshop module 9.
- Part 1 Month 10 Purpose and general framework (CCMP) – As we went through a lot of topics with the last nine workshops and went from a general approach to a punctual deep dive, we now want to establish your new CCMP within the last three workshops. We start with the general framework and prepare our document carefully in a step-by-step guide. Therefore, we will learn all necessary vocabulary first and define critical sources, abbreviations and definitions. A clear, company-wide understanding will be critical for your future. How to handle any changes might sound simple but you know that the guidelines for this must be strict and that is why we are here to discuss it and bring it to one result. At least you will have your own management plan template at the end of the workshop and the headlines are clear. You can go ahead in workshop 11 and define your individual response structure.
- Part 1 Month 11 Response Structure (CCMP) – The main organization groups, roles, persons and responsibilities as well as lines of communication will be represented in a graphic depicting the hierarchical structure.
- Part 1 Month 12 Response Continuous Process and Logistics (CCMP) – With workshop module 12 you will create the big picture on your way to cyber resilience. But no success if the effectiveness of working together in a crisis is not prepared in detail. That is why we will create a template and concrete messages for your company played out when it comes to day zero. This detailed action plan is like the medicine on your nearest shelf. It helps you to be focused, reduces stress in the very first part of an upcoming cyber crisis and will give you the first boost to manage it as best as possible. But what if all we analyzed, discussed and created just stays here? We will talk about how to implement a permanent project management to roll out your cyber crisis management plan. The role of the project management team, where to situate it and who are the project sponsors. These are the last critical questions and at the end of twelve one day workshops, you will be glad to invest your time because your output is ready for implementation at much lower costs a crisis (out of joint) could cause.
Methodology
Destination Resilience
Program planning:
The program consists of twelve workshops. Whereas in the workshops one to nine we point out different specific aspects of cyber crisis management planning and deep dive into it, we create your own cyber crisis management plan (CCMP) during the last three workshops. We follow the logic of the cyber resilience cycle from prepare, prevent, protect, respond, recover and then compose it all together matching your individual company structure, situation and needs. We also distinguish between internal and external as well as soft and hard skills to go through a holistic approach touching all relevant resources of your company. You will see that we will identify key stakeholders as well as your crown jewels to priorities your approach in the dimensions: Time/Speed, Costs and Impact. Each workshop has a theoretical and at least one practical part, which output can be used for the next workshops and is already useful for your company.
Program development:
Those companies which belong to the pre certified program have the benefit to set better focus areas and decide about the content percentages of each section. By screening the success factors of highly efficient companies we can adapt these solutions to your company and consider a pathway for implementation. We can use a questionnaire to check if the expectations of the participants have been fulfilled.
Program implementation:
Setting the right implementation structure and giving advises as well as templates, checklists and workarounds, you and your project management team will be ready for implementation. It is also included to set up a training plan for frequent fresh ups and to maximize the coverage off trained staff. This will guarantee a long-time ever-growing resilience.
Program review
There will be several milestones to review the benefits of the program. Starting with the evaluation of each workshop as well as the confrontation from workshop outputs with your operational teams inside the company. Second, after the cyber crisis management plan has been established virtually, it will take you about 3 to 9 months to implement the developed structure, contents and guidelines. Meaning after two years you can evaluate, if the implementation was successful and how to get from a “re-setup” into a living model. Of course, each plan is only as good, as it was needed. Hopefully the successful program leads to less threats and risk, which can be evaluated with stress tests and audits later. The program is an ignition and a framework already individualized. Thus, a long-time guidance will be key for its success.
Figure 4 Roadmap to Resilience: General Structure
Figure 5 First Six Modules
Figure 6- Second Half – With Last Three Modules of Crisis Management Plan (CCMP) Creation
Industries
This service is primarily available to the following industry sectors:

Consumer Goods
The challenge for the Consumer Industry is the ever-growing raise of product launches and with this a time relevant question of success. Second the percentage of online sales is much higher than in earlier days. So, a lot of business are almost fully digital and the customer relationship management and database is the “gold” of every company in this sector.
FMCG companies are aware of cyberattacks and they use service companies, consultancy, audits and various risk reducing solutions. Managing cyber risk is a complex and evolving challenge for industries across the globe. As technology advances and cyber threats become more sophisticated, organizations face a growing list of challenges in their efforts to protect their digital assets and maintain the resilience of their operations.
Some of the current industry challenges in managing cyber risk include:
• Advanced Persistent Threats (APTs): These are sophisticated, prolonged cyber-attacks carried out by well-funded and highly skilled attackers, often with specific targets and objectives. They can be difficult to detect and even more challenging to mitigate.
• Insider Threats: Employees or contractors with legitimate access to an organization’s systems can intentionally or unintentionally cause security breaches. Managing insider threats requires a delicate balance between enabling productivity and maintaining security controls.
• Ransomware: Ransomware attacks have become increasingly common and can cripple an organization’s operations by encrypting critical data and demanding payment for the decryption key. The rise of ransomware-as-a-service has made such attacks more accessible to a broader range of attackers.
• Supply Chain Attacks: Cybercriminals target third-party vendors and suppliers to gain access to an organization’s network indirectly. These attacks can be difficult to prevent because they exploit trust relationships within the supply chain.
• IoT and OT Security: The proliferation of Internet of Things (IoT) devices and Operational Technology (OT) systems in industrial and enterprise environments introduces new attack vectors. Many of these devices have inadequate security measures, making them easy targets for cybercriminals.
• Cloud Security: As organizations migrate to cloud services, they face new challenges in managing access controls, data privacy, and compliance. Cloud environments can be more complex to secure due to their shared responsibility model and the need for robust identity and access management (IAM).
• Regulatory Compliance: Keeping up with an ever-changing landscape of cybersecurity regulations and standards can be daunting. Organizations must navigate a complex web of local, national, and international laws that govern data protection and privacy.
• Skills Gap: There is a significant shortage of cybersecurity professionals with the necessary skills to manage cyber risk effectively. This skills gap can leave organizations vulnerable to attacks.
• Cybersecurity Awareness: Despite efforts to improve cybersecurity awareness, social engineering and phishing attacks remain highly effective. Educating employees and users about safe practices is an ongoing challenge.
• Zero-Day Exploits: These are attacks that target previously unknown vulnerabilities in software. Since there is no patch available at the time of the attack, zero-day exploits can be particularly damaging.
• Data Privacy Concerns: With the rise of data-driven business models, protecting sensitive information has become a top priority. Organizations must ensure that they are not only securing data but also respecting user privacy and consent.
• Third-Party Risk Management: Organizations must also consider the cybersecurity practices of their partners and vendors. A breach in a third-party system can have a ripple effect, impacting all associated organizations.
• Artificial Intelligence and Machine Learning: While AI and ML can enhance cybersecurity defenses, they can also be used by attackers to create more sophisticated threats, such as polymorphic malware that can evade traditional detection methods.
• Resource Constraints: Cybersecurity requires significant investment in technology, people, and processes. Many organizations struggle to allocate sufficient resources to keep up with the pace of cyber threats.
Addressing these challenges requires a multi-faceted approach, including robust cybersecurity strategies, investment in technology and human resources, ongoing risk assessments, and a commitment to continuous improvement in cybersecurity practices.
Infosys commissioned a study of 113 senior executives from the Consumer-Packaged Goods and Retail (CPG&R) industry with revenues of over USD 500 million across the US, Europe, Australia and New Zealand (ANZ). The respondents were senior executives involved in cybersecurity initiatives representing both technology and business functions. The survey was aimed at understanding the cybersecurity initiatives for Consumer-Packaged Goods and Retail companies. Some interesting findings are:
• 65% in the CPG&R industry have a well-defined enterprise-wide strategy/roadmap implemented
• A rising wave of cybercrimes has the CPG&R industry concerned chiefly about hackers and hacktivists (83%), corporate espionage (81%), and insider threats (74%)
• The top three problems that enterprises face are embedding security in the enterprise IT architecture (73%), building a security-first culture (72%) and keeping pace with fast-changing cyber technologies (64%)
• Working with technology vendors and service providers (56%), training and certification (50%) and workshops and enablement sessions (48%) are the top methods that CPG&R enterprises employ for overcoming the challenges they face
• The CPG&R industry is currently enhancing their cybersecurity program with Artificial intelligence (46%), Blockchain technology (43%) and Behavioral analytics (33%)
With our program we will optimize the critical success factors and reduce your risk.

Media and Marketing
The media and marketing sectors face unique challenges in managing cyber risk due to the nature of their work, which often involves handling large volumes of sensitive data, including personal information, intellectual property, and confidential business strategies.
Here are some of the current challenges these industries face:
Data Breaches and Privacy Concerns:
• Media and marketing companies often store vast amounts of personal data, making them attractive targets for cybercriminals seeking to exploit or sell this information.
• Compliance with data protection regulations such as the General Data Protection Regulation (GDPR) in the EU, the California Consumer Privacy Act (CCPA), and others is a significant challenge, as these laws impose strict requirements on how personal data is collected, stored, and processed.
Advanced Cyber Threats:
• These sectors must contend with sophisticated cyber threats like phishing, spear phishing, and social engineering attacks that target employees to gain access to sensitive information.
• The rise of fileless malware and advanced persistent threats (APTs) that can evade traditional security measures also poses a significant risk.
Supply Chain Vulnerabilities:
• Media and marketing firms often rely on third-party vendors and suppliers, which can introduce vulnerabilities if those partners have inadequate cybersecurity practices.
• A breach in the supply chain can affect the entire network, leading to a loss of data and reputation.
Remote Work and BYOD Policies:
• The increasing trend of remote work and bring-your-own-device (BYOD) policies has expanded the attack surface for cybercriminals.
• Ensuring the security of remote access and personal devices that handle company data is a complex challenge.
Content Management Systems (CMS) Vulnerabilities:
• Many media companies use CMS platforms to publish content, which can be targeted by hackers looking to deface websites, steal data, or distribute malware.
• Keeping CMS platforms and plugins up to date with the latest security patches is crucial but can be overlooked.
Digital Advertising Threats:
• The digital advertising ecosystem is complex, with ads often sourced from multiple ad networks and exchanges. This complexity can introduce malware and malvertising (malicious advertising) risks.
• Click fraud and ad fraud can also impact the effectiveness and cost of marketing campaigns.
Intellectual Property Theft:
• Media and marketing agencies often deal with creative content and strategic plans that are valuable intellectual property.
• Protecting this IP from theft or unauthorized use is a significant concern, especially in a digital environment where information can be easily copied and distributed.
Social Media Risks:
• Social media platforms are a double-edged sword for marketing, providing opportunities for engagement but also risks such as impersonation, fake accounts, and the spread of misinformation.
• Managing the security of social media accounts and protecting against unauthorized access is a growing challenge.
Cybersecurity Awareness and Training:
• Employees in media and marketing may not always be aware of the cybersecurity risks associated with their daily tasks, such as sharing content or engaging with audiences online.
• Ongoing training and awareness programs are essential to mitigate the risk of human error leading to a security breach.
Regulatory and Compliance Pressures:
• In addition to data protection regulations, media and marketing companies must navigate various industry-specific regulations that impact their cybersecurity practices.
• The cost and complexity of compliance can be a significant challenge, especially for global organizations operating in multiple jurisdictions.
To address these challenges, media and marketing organizations must invest in robust cybersecurity infrastructure, adopt a culture of security awareness, and stay informed about the latest threats and best practices in the industry. Additionally, they should consider implementing advanced security solutions, such as AI-driven threat detection and response systems, to stay ahead of evolving cyber threats.
Version 1 Sector Impact Dial is a guide to key trends and challenges, how to deal with them and rise to the challenge of embracing an increasingly digital world.
The global media market is predicted to grow to over $2.9tn by 2026 from around $1.9tn in 2017, a near 50% growth in just under a decade. Other research predicts a 4-5% onward compound annual growth rate. So, there is ample opportunity for media organizations to grow, adapt and embrace the macro forces impacting the sector. The dial covers a large number of topics and each is covered in turn to explore the major trends we have identified as most impactful to media and publishing today.
With our program we will optimize the critical success factors and reduce your risk.

Digital
The digital sector, which includes industries such as software development, IT services, e-commerce, and digital content creation, faces a rapidly evolving landscape of cyber risks. The nature of the digital sector, with its reliance on cloud computing, internet-connected devices, and large volumes of data, presents unique challenges in managing cyber risk.
Raising cyber resilience in the digital sector involves enhancing the ability of organizations to prevent, detect, and recover from cyberattacks. While there are numerous strategies and technologies available to improve resilience, several challenges make this task complex and ongoing. Here are some of the current challenges to raising cyber resilience in the digital sector:
Keeping Pace with Threat Evolution: Cyber threats are constantly evolving, with attackers developing new techniques to exploit vulnerabilities. Staying ahead of these threats requires continuous learning and adaptation.
Integrating Cybersecurity into Digital Transformation: As organizations undergo digital transformation, integrating cybersecurity from the outset is crucial. This includes securing new technologies, platforms, and processes as they are adopted.
Managing a Distributed Workforce: The rise of remote work has expanded the attack surface. Ensuring that all employees, regardless of location, follow secure practices and have access to necessary security tools is a significant challenge.
Securing the Supply Chain: Digital sector companies rely on a complex network of suppliers and partners. Ensuring that all components of the supply chain are secure and that third-party risks are managed is an ongoing challenge.
Addressing the Skills Gap:There is a shortage of cybersecurity professionals with the skills needed to implement and maintain resilient systems. Training and retaining talent is critical.
Balancing Security with Usability: Security measures should not impede productivity or user experience. Finding the right balance between security controls and usability is a constant challenge.
Implementing Zero Trust Principles: The zero trust model, which assumes breach and verifies every access attempt, is a shift from traditional security perimeters. Implementing zero trust across the digital sector requires significant changes to security architectures and practices.
Protecting Against Insider Threats: Insiders with malicious intent or those who unintentionally cause security incidents pose a significant risk. Detecting and mitigating insider threats requires careful monitoring and access controls.
Ensuring Data Privacy and Compliance: With increasing regulations such as GDPR, CCPA, and others, organizations must ensure that data is handled securely and in compliance with legal requirements, which can be complex and vary by jurisdiction.
Investing in Cybersecurity Infrastructure: Cyber resilience requires investment in advanced security technologies, such as AI-driven threat detection, encryption, and multi-factor authentication. Budget constraints can limit the implementation of such technologies.
Recovering from Cyber Incidents: Having robust incident response and recovery plans is essential. However, the complexity of modern IT environments and the need for quick recovery to minimize downtime make this a significant challenge.
Managing Cyber Insurance: Cyber insurance can help mitigate the financial impact of cyber incidents, but navigating the terms, conditions, and coverage requirements can be complex. Additionally, insurers are increasingly scrutinizing cybersecurity practices before offering coverage.
Cultivating a Security-First Culture: Employee awareness and buy-in are critical for cyber resilience. Cultivating a culture where security is everyone’s responsibility can be challenging but is essential for long-term resilience.
Adapting to New Technologies: Emerging technologies such as 5G, IoT, AI, and quantum computing bring new security considerations. Understanding and mitigating the risks associated with these technologies is an ongoing challenge.
Global Threat Landscape: The digital sector operates in a global context, and threats can originate from anywhere. Coordinating defense strategies and sharing threat intelligence across borders is complex but necessary for resilience.
To address these challenges, digital sector companies need to adopt a proactive and layered security approach, invest in employee training and awareness, leverage advanced security technologies, and foster a culture of security that is adaptable to the ever-changing threat landscape. Addressing these challenges requires a multi-faceted approach, including investment in technology, training, and processes, as well as fostering collaboration within the industry and with cybersecurity experts.
Prior to the COVID-19 pandemic, digital transformation largely focused on customer experience. Then, everything changed—and accelerated. Now, digital transformation is the centerpiece of operational efficiency and innovation across the organization.
With our program we will optimize the critical success factors and reduce your risk.

Logistics
The logistics industry, which encompasses transportation, warehousing, distribution, and supply chain management, faces several unique challenges in managing cyber risk. As logistics operations become increasingly digital and interconnected, they become more vulnerable to cyber threats. Here are some of the current logistics challenges in managing cyber risk:
Supply Chain Complexity:
• Logistics involves numerous stakeholders, including suppliers, manufacturers, distributors, and retailers, each with their own cybersecurity practices. A breach in any part of the supply chain can affect the entire network.
• Third-party vendors and partners may have inadequate security measures, creating vulnerabilities that cybercriminals can exploit.
Internet of Things (IoT) and Operational Technology (OT):
• The logistics sector relies heavily on IoT devices for tracking, monitoring, and automation. These devices can be targeted by cyber attackers to disrupt operations or steal sensitive data.
• OT systems, which control physical operations, are also at risk. Compromising these systems can lead to safety incidents, environmental damage, or operational disruptions.
Data Breaches and Privacy Concerns:
• Logistics companies handle a wealth of sensitive information, including customer data, shipping manifests, and financial records. Data breaches can lead to financial loss, legal penalties, and damage to reputation.
• Compliance with data protection regulations such as GDPR, CCPA, and others is a significant challenge, requiring robust data security measures.
Cyber-Physical Systems:
• The integration of cyber elements with physical systems, such as autonomous vehicles and drones, introduces new attack vectors. Cyber-attacks on these systems can lead to safety risks, theft, or disruption of services.
Ransomware and Malware Attacks:
• Logistics companies are prime targets for ransomware attacks, as disruptions can be particularly costly. Malware can also compromise systems, leading to data theft or operational disruptions.
Advanced Persistent Threats (APTs):
• State-sponsored or highly sophisticated cyber attackers may target logistics firms for espionage or to gain strategic advantages, particularly in sectors like defense and high-tech manufacturing.
Insider Threats:
• Employees or contractors with access to logistics systems can intentionally or unintentionally cause security breaches. Insider threats are difficult to detect and require careful management of user privileges and access controls.
Mobile and Remote Workforce:
• The logistics industry often relies on a mobile workforce using various devices and networks. Securing these remote connections and ensuring the protection of data on mobile devices is a complex challenge.
Legacy Systems:
• Many logistics operations still use outdated technology and legacy systems that may not have modern security features. Upgrading these systems can be costly and complex, leaving organizations vulnerable.
Cybersecurity Skills Gap:
• There is a shortage of cybersecurity professionals with the skills needed to secure logistics operations. This gap can leave critical systems unprotected or inadequately monitored.
Regulatory Compliance:
• Logistics companies must navigate a complex web of international regulations and standards, which can vary by region and sector. Keeping up with these requirements while maintaining operational efficiency is a significant challenge.
To address these challenges, logistics companies need to invest in advanced cybersecurity solutions, conduct regular risk assessments, and ensure that their employees are trained in cybersecurity best practices. Additionally, they should foster collaboration with other industry players and cybersecurity experts to share threat intelligence and develop collective defense strategies.
“In 2024, the logistics sector is navigating through a transformative era marked by significant global logistics problems that demand strategic responses from businesses. These challenges, ranging from persistent supply chain disruptions to the seamless integration of advanced technologies, are reshaping the logistics and supply chain management landscape. For companies in New Zealand aiming to maintain or gain a competitive edge, understanding and addressing these challenges is essential. This blog explores the logistics industry’s key hurdles this year and offers examples and practical solutions to help businesses adapt and excel in this evolving environment.” (DHL Group)
DHL Group summarizes four major logistic challenges in 2024:
• Supply Chain Disruptions
• Sustainability and environmental concerns
• Technology integration
• Regulatory and compliance challenges
A younger analysis from Maxima Consulting underlines, that the key challenges in the logistics mainly deal with identity and digitalization. Which emphasis the capability to stay resistant in the digital age and invest in resilience.
With our program we will optimize the critical success factors and reduce your risk.

Defense
Raising cyber resilience in the defense sector is of paramount importance due to the sensitive nature of the information and systems involved. The defense sector is a high-value target for nation-states, cybercriminals, and other malicious actors seeking to gain strategic advantages, steal intellectual property, or disrupt operations.
Here are some of the current challenges to raising cyber resilience in the defense sector:
Advanced Persistent Threats (APTs): Defense systems are frequently targeted by sophisticated attackers, including state-sponsored actors, who employ advanced techniques to evade detection and maintain long-term access to networks.
Supply Chain Vulnerabilities: The defense sector relies on a complex supply chain that includes contractors and vendors. Ensuring the security of the entire supply chain is challenging, as a compromise in any part can lead to vulnerabilities.
Operational Technology (OT) Security: Defense systems often include critical OT that controls physical processes. Securing these systems is complex, as they may use legacy technology that is difficult to update or replace.
Cyber Warfare and Espionage: The defense sector must prepare for cyber warfare scenarios, which can involve sophisticated attacks aimed at disrupting military operations, stealing defense secrets, or undermining national security.
Information Sharing and Collaboration: Balancing the need for information sharing among defense partners with the requirement to protect sensitive data is a significant challenge. Secure collaboration tools and protocols are essential.
Regulatory Compliance and Oversight: Defense contractors and agencies must comply with stringent cybersecurity regulations, such as the Defense Federal Acquisition Regulation Supplement (DFARS) and the Cybersecurity Maturity Model Certification (CMMC). Meeting these standards requires significant effort and resources.
Insider Threats: Insiders with access to defense systems can pose a significant risk. Identifying potential insider threats and implementing controls to mitigate them is a complex task.
Technology Adoption and Integration: Rapidly adopting and integrating new technologies while ensuring they are secure and compatible with existing systems is a challenge in the fast-paced defense environment.
Cybersecurity Skills Gap: The defense sector faces a shortage of cybersecurity professionals with the specialized skills needed to secure military networks and systems.
Training and Exercises: Conducting realistic and effective cyber training and exercises to prepare for potential threats is challenging, especially in a sector where operational security is critical.
Secure Communication Systems: Ensuring that communication systems are secure against interception and tampering is a constant challenge, especially in contested environments.
Data Protection and Privacy: Protecting the vast amounts of data generated by defense operations, including personal information of service members, from unauthorized access or breaches is a significant concern.
Physical Security of Cyber Assets: The defense sector must also ensure the physical security of cyber assets, as the loss or theft of hardware can lead to serious security breaches.
International Collaboration and Conflict: Coordinating cybersecurity efforts with international partners while also being prepared to defend against cyber threats from adversaries adds a layer of complexity to resilience efforts.
Budget Constraints: Allocation of sufficient resources for cybersecurity can be a challenge, as defense budgets may be constrained or prioritize other areas of national security.
Addressing these challenges requires a comprehensive approach that includes advanced technology solutions, rigorous cybersecurity protocols, skilled personnel, and ongoing vigilance to protect against the ever-evolving landscape of cyber threats.
For example, the global cyber warfare market size was valued at USD 33.81 billion in 2022 and projected to grow at a compound annual growth rate (CAGR) of 14.9% from 2023 to 2030. Recently, government and international organizations have become focused on cybersecurity owing to increased security challenges posed by or within cyberspace. It has raised several concerns about national security, thus alarming the need for a robust cybersecurity posture. Thus, the government, military, and other agencies are protecting their digital infrastructure and devices connected to the internet to deter cyber-attacks.
With our program we will optimize the critical success factors and reduce your risk.
Locations
This service is primarily available within the following locations:

Hamburg
Hamburg, Germany’s gateway to the world, is not just a bustling port city but is rapidly becoming a cornerstone in the cybersecurity landscape of Europe.
As the digital age accelerates, cybersecurity has emerged as a pressing concern for both governments and businesses alike. Hamburg, with its rich industrial history and strategic location, is positioning itself as a leader in this critical sector.
A Convergence of Industry and Academia
Hamburg’s transformation into a cybersecurity hub can be attributed to the city’s unique blend of industrial prowess and academic excellence. The presence of major corporations such as Airbus, Siemens, and various shipping giants provides a fertile ground for cybersecurity solutions tailored to diverse sectors. Furthermore, the city’s universities and research institutions are at the forefront of developing cutting-edge technologies.
The University of Hamburg and the Hamburg University of Technology (TUHH) offer specialized courses and research programs in cybersecurity, fostering a new generation of experts who are well-versed in the latest threats and defenses. Partnerships between these academic institutions and industry leaders ensure that theoretical knowledge is rapidly translated into practical applications.
Government Initiatives and Investments
The German government recognizes the importance of cybersecurity and has introduced numerous initiatives to bolster Hamburg’s capabilities. The Federal Ministry for Economic Affairs and Energy has allocated significant funds to support startups and established firms in the cybersecurity domain. These investments are designed to spur innovation and position Hamburg as a global leader in cybersecurity solutions.
One notable initiative is the establishment of the Hamburg Innovation Lab, a state-of-the-art facility where researchers, entrepreneurs, and industry experts collaborate on developing next-generation security technologies. The lab serves as a testing ground for new ideas and a launchpad for startups looking to make their mark in the cybersecurity field.
The Rise of Cybersecurity Startups
Hamburg’s vibrant startup ecosystem is another key factor in its rise as a cybersecurity hub. The city is home to a growing number of innovative startups that are developing advanced solutions to tackle the ever-evolving landscape of cyber threats. Companies like Secucloud, a cloud-based security provider, and Cybus, which focuses on industrial cybersecurity, are just a few examples of the innovative firms that call Hamburg home.
These companies benefit from Hamburg’s robust infrastructure, supportive business environment, and access to a wide range of resources. Incubators and accelerators such as Next Media Accelerator and the Digital Hub Logistics provide invaluable support to young companies, helping them to scale and succeed in the competitive cybersecurity market.
International Collaboration and Global Reach
Hamburg’s strategic location and strong international connections make it an ideal base for cybersecurity firms looking to expand their global reach. The city’s port, one of the largest in Europe, facilitates easy access to international markets, while its extensive digital infrastructure ensures seamless communication and collaboration across borders.
Hamburg also plays a key role in international cybersecurity collaborations. The city regularly hosts conferences and events that bring together experts from around the world to share knowledge and discuss the latest trends and challenges in the field. These events not only enhance Hamburg’s reputation as a cybersecurity hub but also foster valuable relationships that drive innovation and growth.
Future Prospects
Looking ahead, Hamburg’s position as a cybersecurity hub is set to strengthen further. The city’s commitment to fostering innovation, combined with its strategic advantages and supportive environment, makes it an attractive destination for cybersecurity firms and talent from around the world.
As cyber threats continue to grow in complexity and frequency, the need for robust cybersecurity solutions will only increase. Hamburg, with its unique blend of industry, academia, and innovation, is well-placed to meet this challenge and emerge as a global leader in cybersecurity.
In conclusion, Hamburg’s rise as a cybersecurity hub is a testament to the city’s forward-thinking approach and its ability to adapt to the demands of the digital age. By leveraging its strengths and seizing opportunities, Hamburg is not only safeguarding its own future but also contributing to the global effort to combat cyber threats.
Berlin
Berlin, the vibrant heart of Germany, has long been recognized for its rich history, cultural diversity, and thriving startup ecosystem. Recently, however, it has also begun to establish itself as a formidable player in the global cybersecurity landscape. With a unique blend of government support, academic prowess, and entrepreneurial zeal, Berlin is rapidly becoming a key hub for cybersecurity innovation.
Government Initiatives and Support
The German government has been proactive in fostering a robust cybersecurity infrastructure. Recognizing the increasing threats in the digital space, Berlin has become a focal point for national cybersecurity initiatives. The government not only sets security standards but also collaborates with local tech firms to develop advanced cybersecurity solutions.
Furthermore, Berlin benefits from significant European Union funding aimed at bolstering cybersecurity across member states. These funds are channeling into research and development, fostering collaboration between public and private sectors, and directly supporting cybersecurity startups.
Academic Excellence and Research
Berlin is home to some of the leading universities and research institutions in Europe, such as the Technical University of Berlin. These institutions are at the forefront of cybersecurity research, exploring areas like cryptography, network security, and artificial intelligence. The city’s academic environment is enriched by a steady influx of international talent, driven by Berlin’s reputation as a progressive and inclusive metropolis.
Collaborations between academia and industry are particularly strong in Berlin, with numerous joint ventures and research projects aimed at tackling the latest cybersecurity challenges. This symbiotic relationship ensures that theoretical advancements quickly translate into practical applications, keeping Berlin at the cutting edge of cybersecurity technology.
Startup Ecosystem and Innovation
Berlin’s startup ecosystem is one of the most dynamic in Europe, characterized by a spirit of innovation and a willingness to tackle complex problems. The city is home to a growing number of cybersecurity startups, ranging from early-stage ventures to more established firms. Companies like Cure53 or Security Research Labs are making significant strides in areas such as penetration testing, vulnerability assessment, and malware analysis.
The city’s numerous accelerators and incubators, such as the Hasso Plattner Institute and the Berlin Startup Scholarship, provide crucial support to these startups. These programs offer not only funding but also mentorship, networking opportunities, and access to cutting-edge technology. This nurturing environment allows cybersecurity startups to thrive and scale, contributing to Berlin’s reputation as a hotbed of innovation.
Challenges and Future Prospects
Despite its many strengths, Berlin faces challenges in its quest to become a global cybersecurity leader. The rapidly evolving nature of cyber threats means that continuous investment in research and development is essential. Additionally, there is a need for greater collaboration on an international level to address the global nature of cyber threats.
Looking ahead, Berlin’s prospects in the cybersecurity domain remain bright. The city’s combination of government support, academic excellence, and entrepreneurial drive positions it well to tackle future challenges and opportunities. As cyber threats continue to grow in both complexity and scale, Berlin’s role as a center for cybersecurity innovation will become increasingly critical.
In conclusion, Berlin is not just a historical and cultural capital but is swiftly emerging as a pivotal player in the cybersecurity arena. With its unique blend of resources and talent, the city is poised to make significant contributions to global cybersecurity efforts, ensuring a safer digital future for all.

Bonn
Bonn Emerges as a Cyber Security Stronghold: A New Era for Digital Defense
In the heart of Germany, the city of Bonn is rapidly becoming a beacon of innovation and resilience in the realm of cyber security. Once the capital of West Germany, Bonn is now leveraging its historical significance and strategic position to carve out a critical role in the global fight against cyber threats.
A Strategic Pivot
Bonn’s transformation into a cyber security hub is no accident. The city has strategically pivoted to address the growing concerns of digital threats that loom over governments, businesses, and individuals alike. This shift is underscored by the presence of several high-profile institutions and initiatives dedicated to cyber security.
Among these, the establishment of the Cyber Security Cluster Bonn stands out. This initiative brings together a consortium of public and private sector entities, including the Federal Office for Information Security (BSI), the Deutsche Telekom Security GmbH, and various academic institutions like the Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE). The cluster aims to foster collaboration, drive research, and develop innovative solutions to the ever-evolving landscape of cyber threats.
Government and Industry Collaboration
The synergy between government agencies and private enterprises in Bonn is a testament to the city’s comprehensive approach to cyber security. The Federal Office for Information Security, headquartered in Bonn, plays a pivotal role in shaping Germany’s national cyber defense strategy. Its proximity to key industry players facilitates seamless collaboration, ensuring that policies are informed by the latest technological advancements and threat intelligence.
Deutsche Telekom, one of the world’s leading integrated telecommunications companies, has also anchored its security operations in Bonn. The company’s security unit, Telekom Security, is at the forefront of developing cutting-edge technologies and services designed to protect critical infrastructure and enterprise networks from sophisticated cyber-attacks.
Academic Excellence Fuels Innovation
Bonn’s academic institutions are equally integral to the city’s cyber security ecosystem. The University of Bonn, renowned for its research prowess, offers specialized programs in cyber security and information technology. These programs are designed to equip the next generation of cyber security professionals with the skills needed to tackle complex digital threats.
Additionally, the Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE) is a key player in Bonn’s cyber security landscape. The institute conducts advanced research in areas such as cryptography, secure communication, and cyber defense, contributing valuable knowledge and expertise to the broader community.
Global Implications
Bonn’s rise as a cyber security stronghold holds significant implications on a global scale. As cyber threats become increasingly sophisticated and pervasive, the need for robust defense mechanisms is more critical than ever. Bonn’s integrated approach, combining government oversight, industry innovation, and academic excellence, serves as a model for other cities and nations striving to bolster their cyber security capabilities.
Moreover, Bonn’s initiatives have the potential to influence international cyber security policies and practices. The city’s collaborative framework can inspire similar partnerships worldwide, fostering a united front against the growing menace of cyber crime.
Looking Ahead
As Bonn continues to solidify its position as a leader in cyber security, the city’s impact will undoubtedly extend beyond national borders. The innovations and strategies developed here will contribute to a safer digital world, protecting the integrity of information systems and the privacy of individuals globally.
In an era where cyber threats are a constant and evolving challenge, Bonn’s proactive stance and commitment to excellence in cyber security offer hope and a blueprint for a secure digital future.

Düsseldorf
In the rapidly evolving landscape of cyber threats and digital transformation, Düsseldorf is carving out a significant niche as a burgeoning hub for cyber security in Europe. This development is not just a testament to the city’s strategic foresight but also a reflection of Germany’s broader commitment to fortifying its digital infrastructure and economy.
Strategic Positioning and Infrastructure
Düsseldorf, the capital of North Rhine-Westphalia, has long been recognized for its robust economic infrastructure, hosting several global corporations. The city’s strategic location, with proximity to major European markets, has made it an attractive destination for businesses. Leveraging this advantage, Düsseldorf has been proactive in building a formidable cyber security ecosystem. The city boasts state-of-the-art data centers and a highly developed IT infrastructure, which are critical in attracting cyber security firms and talent.
Government Initiatives and Support
The German government has played a pivotal role in bolstering Düsseldorf’s cyber security credentials. With initiatives such as the Digital Strategy 2025 and substantial investments in cyber security research, Germany aims to position itself as a leader in digital security. Düsseldorf has been a prime beneficiary of these policies, receiving funding for various cyber security projects and research institutions. The city’s universities and technical institutes are increasingly focusing on cyber security, producing a skilled workforce ready to tackle the challenges of the digital age.
Industry Collaboration and Innovation.
One of Düsseldorf’s key strengths lies in its collaborative approach to innovation. The city hosts numerous cyber security conferences, workshops, and hackathons, fostering a culture of continuous learning and innovation. These events provide a platform for industry leaders, startups, and academia to exchange ideas and develop cutting-edge solutions.
Rise of Startups and Investment Opportunities
Düsseldorf’s vibrant startup ecosystem is another critical factor in its ascent as a cyber security hub. The city is home to several innovative startups specializing in various aspects of cyber security, from threat intelligence to blockchain security. These startups benefit from a supportive environment that includes incubators, accelerators, and access to venture capital. Investors are increasingly recognizing the potential of Düsseldorf’s cyber security sector, leading to a surge in funding and partnerships.
Challenges and the Road Ahead
Despite its impressive strides, Düsseldorf faces challenges typical of any emerging tech hub. The rapidly changing nature of cyber threats necessitates continuous adaptation and innovation. There is also a pressing need to address the talent gap in cyber security, ensuring that the workforce keeps pace with technological advancements. However, with its strong foundation, strategic initiatives, and a collaborative ecosystem, Düsseldorf is well-positioned to overcome these challenges and cement its status as a leading cyber security hub.
Düsseldorf’s journey in the cyber security domain is a compelling narrative of strategic vision, collaboration, and innovation. As cyber threats become increasingly sophisticated, the city’s role in safeguarding digital infrastructure will only grow in significance. For businesses and investors looking to be at the forefront of cyber security, Düsseldorf offers a unique blend of opportunity, talent, and infrastructure. In the years to come, this dynamic city is poised to play a crucial role in shaping the future of cyber security in Europe and beyond.

Hannover
Hannover Emerges as a Cyber Security Hub Amid Rising Digital Threats
Once renowned for its industrial prowess and trade fairs, Hannover is swiftly evolving into a pivotal player in the cyber security landscape. As digital threats escalate globally, this German city is positioning itself at the forefront of cyber defense innovation, bolstering both its economy and security infrastructure.
A Strategic Pivot Towards Cyber Security
Hannover’s transformation can be attributed to strategic investments and collaborative efforts between the government, academia, and private sector. The Lower Saxony state government has committed significant resources to fostering a robust cyber security ecosystem. This includes funding for research institutions, subsidies for tech startups, and initiatives to attract top-tier talent.
The establishment of the Hannover Cyber Security Research Center exemplifies this commitment. The center, a joint venture between the Leibniz University Hannover and several industry partners, focuses on cutting-edge research in artificial intelligence, encryption technologies, and threat detection systems. By bridging the gap between theoretical research and practical application, the center aims to produce innovative solutions that address real-world cyber threats.
Industry Collaboration and Innovation
Hannover’s industrial heritage has provided a solid foundation for its cyber security ambitions. The city’s robust manufacturing sector, dominated by firms specializing in automotive, engineering, and logistics, has a vested interest in cyber security. Protecting critical infrastructure and intellectual property from cyber threats is paramount, driving these industries to collaborate closely with cyber security experts.
Leading corporations such as Volkswagen and Continental have established cyber security units in Hannover, leveraging local expertise to safeguard their operations. These units are not only focused on defensive measures but are also developing proactive strategies to predict and mitigate potential threats. This proactive stance is crucial in an era where cyber attacks are becoming increasingly sophisticated and targeted.
Educational Excellence and Talent Development
A key factor in Hannover’s rise as a cyber security hub is its focus on education and talent development. The Leibniz University Hannover offers specialized programs in cyber security, attracting students from across the globe. These programs are designed to equip students with the skills and knowledge required to tackle contemporary cyber challenges.
Moreover, Hannover’s educational institutions have fostered partnerships with industry leaders, ensuring that the curriculum remains relevant and aligned with industry needs. Graduates from these programs are in high demand, often securing positions in prestigious companies even before completing their studies.
Global Recognition and Future Prospects
Hannover’s efforts have not gone unnoticed on the global stage. The city hosted the International Cyber Security Conference, drawing experts and policymakers from around the world. The conference served as a platform to showcase Hannover’s advancements in cyber security and facilitated valuable exchanges of knowledge and best practices.
Looking ahead, Hannover’s trajectory in the cyber security domain appears promising. With continued investment, innovation, and collaboration, the city is well-positioned to address the evolving landscape of digital threats. As cyber security becomes an integral part of national and economic security, Hannover’s role as a leading hub in this field will undoubtedly grow.
Hannover’s strategic pivot towards cyber security represents a significant shift in the city’s industrial landscape. By leveraging its rich industrial heritage, fostering educational excellence, and promoting industry collaboration, Hannover is emerging as a critical player in the global cyber security arena. As digital threats continue to rise, the city’s proactive and innovative approach will be instrumental in safeguarding both national and international interests.
Program Benefits
Management
- Strategic approach
- Cost Savings
- Business Continuity
- Risk Management
- Reputation Protection
- Clear Responsibilities
- Crisis Preparation
- Competitive Advantage
- Playbook development
- Process Transparency
Human Resources
- Employee Awareness
- Efficient communication
- Set Responsibilities
- Threat Awareness
- Reduce fluctuation
- Better contracts
- Less Stress
- Secure workstation
- Stable organization
- Easy understanding
Legal
- Regulatory Compliance
- Risk Mitigation
- Security Management
- Framework knowledge
- Correct communication
- Temporal conditions
- Legal conditions
- Broadening the perspective
- Management Cooperation
- Focus Areas
Testimonials

To be advised.
More detailed achievements, references and testimonials are confidentially available to clients upon request.
Client Telephone Conference (CTC)
If you have any questions or if you would like to arrange a Client Telephone Conference (CTC) to discuss this particular Unique Consulting Service Proposition (UCSP) in more detail, please CLICK HERE.